ESET, the leader in proactive protection against Internet threats with a 20 year history, has discovered a social engineering trojan horse. The piece of malware was managed to steal the login credentials of more than 16,000 Facebook users. The focus of the malware was on stealing personal Facebook (FB) login details and linking these with the user statistics of Texas HoldEm Poker, in case the victim plays this game. The detection stats of ESET have shown that the threat was spreading almost exclusively in Israel. It needs to be added that the targeted application is a legitimate and very popular FB application by Zynga Inc. According to AppData, the application has a monthly share of 35 million active users.ESET began studying the Trojan at the beginning of 2012. However, thanks to proactive generic detection of this threat, the users of ESET security solutions were protected against it already from December 2011. As the detection stats have shown that the threat disseminated primarily in Israel, ESET has contacted Israeli CERT (Computer Emergency Response Team) as well as Israeli police in early 2012. During the investigation we could not provide any details about this threat publicly and presently this threat has been deactivated.
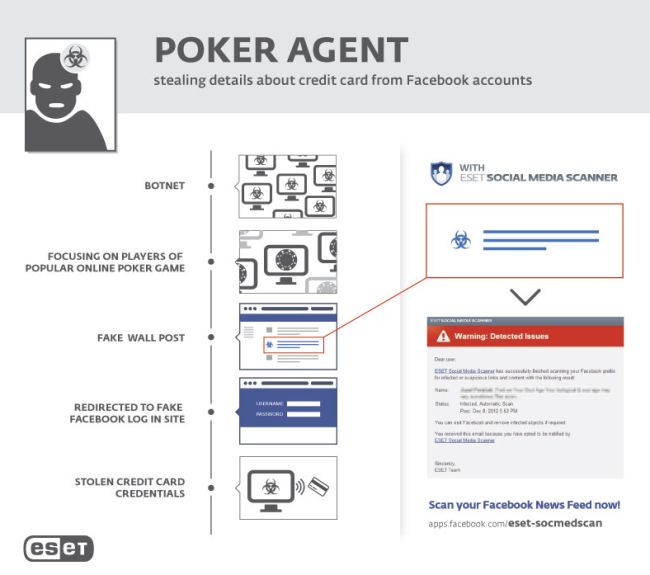
The attacker used the malware to gain the user’s FB login credentials, his/her score in the game, as well as information on the amount of credit cards stored in his/her Facebook settings and available to increase the credit in the game of poker. The game had a functionality that allowed replenishing the chip value using real money by inputting the credit card details or PayPal account. To gain the user’s login credentials, an army of 800 of computers were used – all infected and controlled by the attacker. These machines were executing commands from the C&C (Command&Control) server. The creator of the threat has launched an attack using the login credentials of several FB accounts, which were gained ahead of time."To protect against attacks relying on social engineering methods, having a good security solution is not enough, users should be attentive to any such ploys,"says Róbert Lipovský, ESET Security Intelligence Team Lead. He adds “The user could recognize the fake FB login page if he/she would check the site’s URL.”The infected computers received a command to login into the user’s FB accounts and to gain the user’s Texas HoldEm score, as well as the amount of credit cards stored in his/her FB account. In case of a user w/o a credit card or low score, the infected computer received instructions to infect the victim’s FB profile with a link to a phishing site. This site has acted to directly or indirectly lure the player’s FB friends to a website resembling the FB homepage. In case the login credentials were input by them, they were also harvested by the attacker. While analyzing this botnet ESET estimates that the attacker could gain access to a total of 16,194 login credentials. ESET would like to caution that any other FB application could have been infected in this way, not just Texas HoldEm Poker.The number of threats utilizing Facebook is rapidly growing. To counter this trend, ESET has introduced a security application ESET Social Media Scanner which is available free of charge and is capable of scanning the user’s profile for the presence of malicious and phishing links. On top of that, the app can detect malicious links on the timeline of user’s Facebook friends.
Source: ESET News
© 2011-2025 All rights reserved