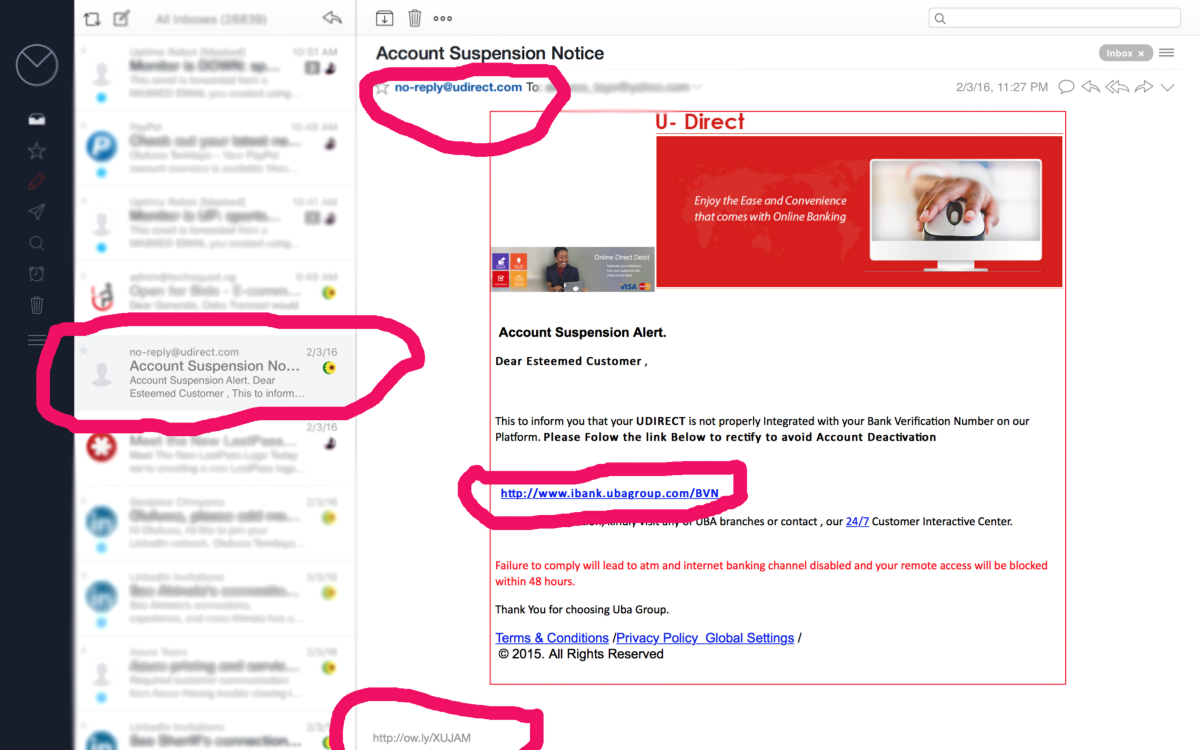
I almost fell for this scam email even with my years of Information Security Research and Ethical Hacking. The reasons I almost fell for this scam are simply because.
I am a UBA customer and I use their prepaid card for online transactions.
The from name is no-reply@udirect.com ( not the actual email address but the name of the sender).
The email is properly formatted.
The real Url is masked under http://www.ibank.ubagroup.com/BVN (Here is the real URL masked http://ow.ly/XUJAM).
The User interface is almost like the real one.
When I clicked on the URL It took me to this fake website below.
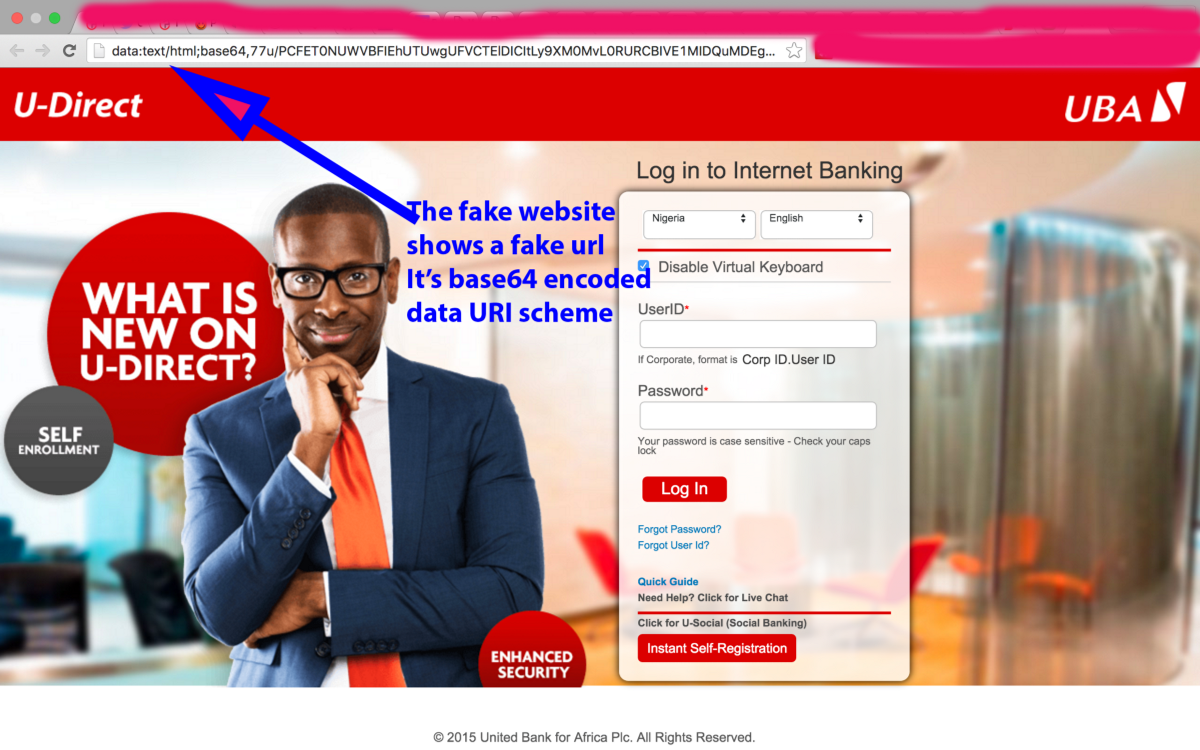
Here is the original Website with Https Secured, padlock and a green color.
Nigerian cybercriminals are upping their game every day and getting sophisticated with new tools and technologies to aid their operations. First this email contains an ow.ly link that redirects twice before reaching the final destination.
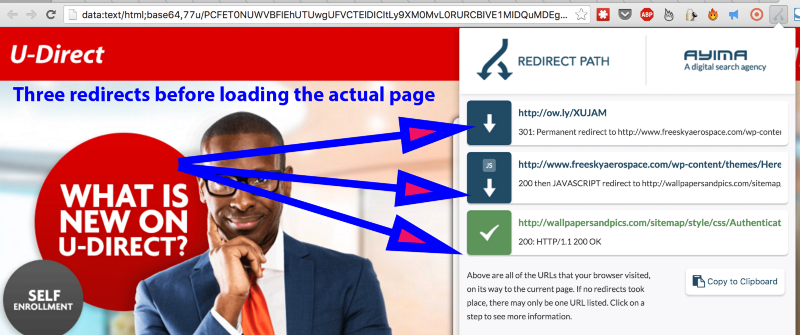
The first redirect was to this hacked website “http://www.freeskyaerospace.com/wp-content/themes/Hereisworld/fontawesome/less/spcsless.php”

Here is the first hacked website showing the directory. Here we can see the spcsless.php file that now redirects to another website.
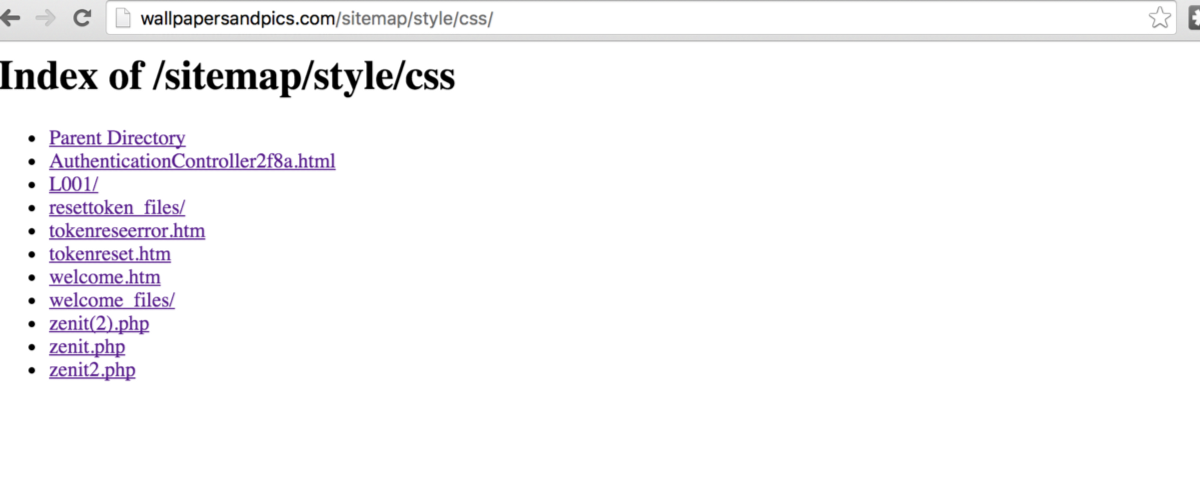
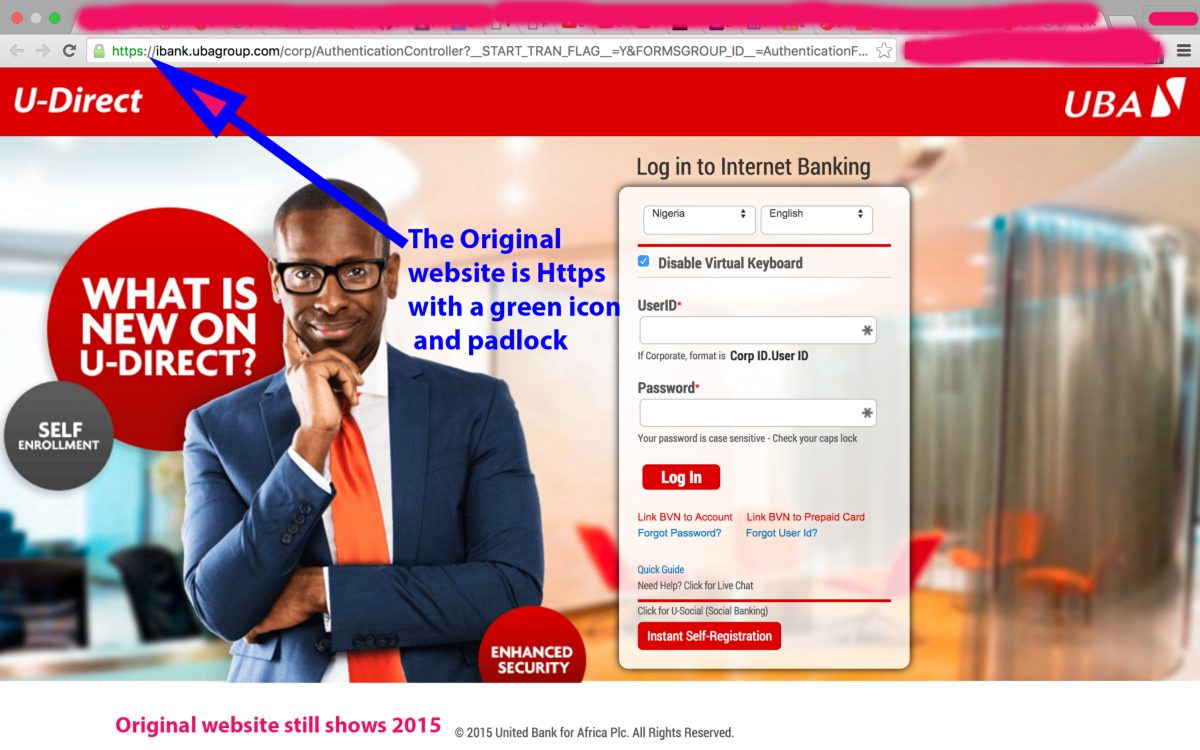
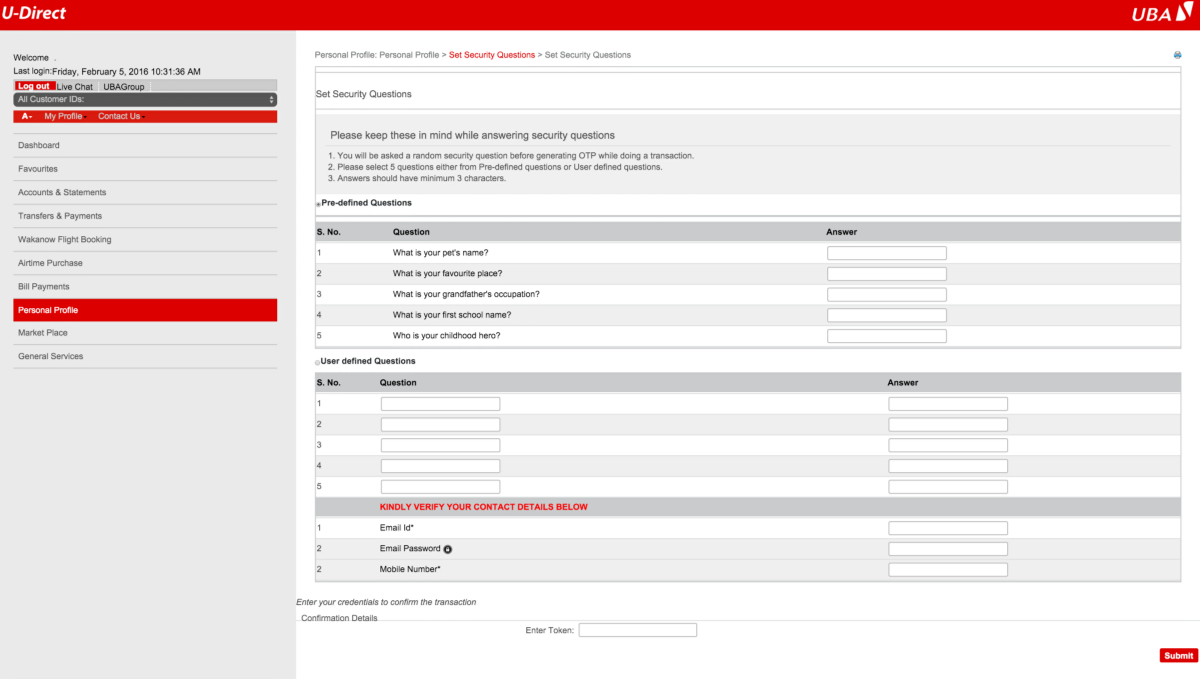
This later redirected to a base64 encoded data URI which loads the web page on the victim’s system so no matter if all the websites involved are taken down the final website resides on the victim’s page. Once you finally log in to the website it shows this page asking users to enter their security questions including their token.
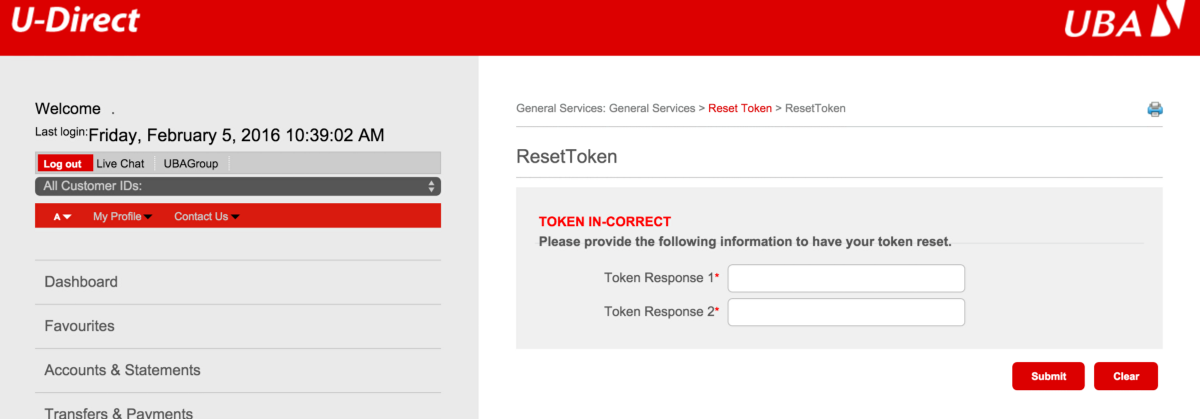
Even after users fill in their details it takes them to this next page asking for their token. No matter how many times users enter their token it keeps showing an error message. If the Bank token is actually Time-based One-time Password Algorithm (TOTP) then I believe the attacker would be getting this data over an instant protocol like XMPP or IRC. If this is the case then I believe this is an organized cyber crime.
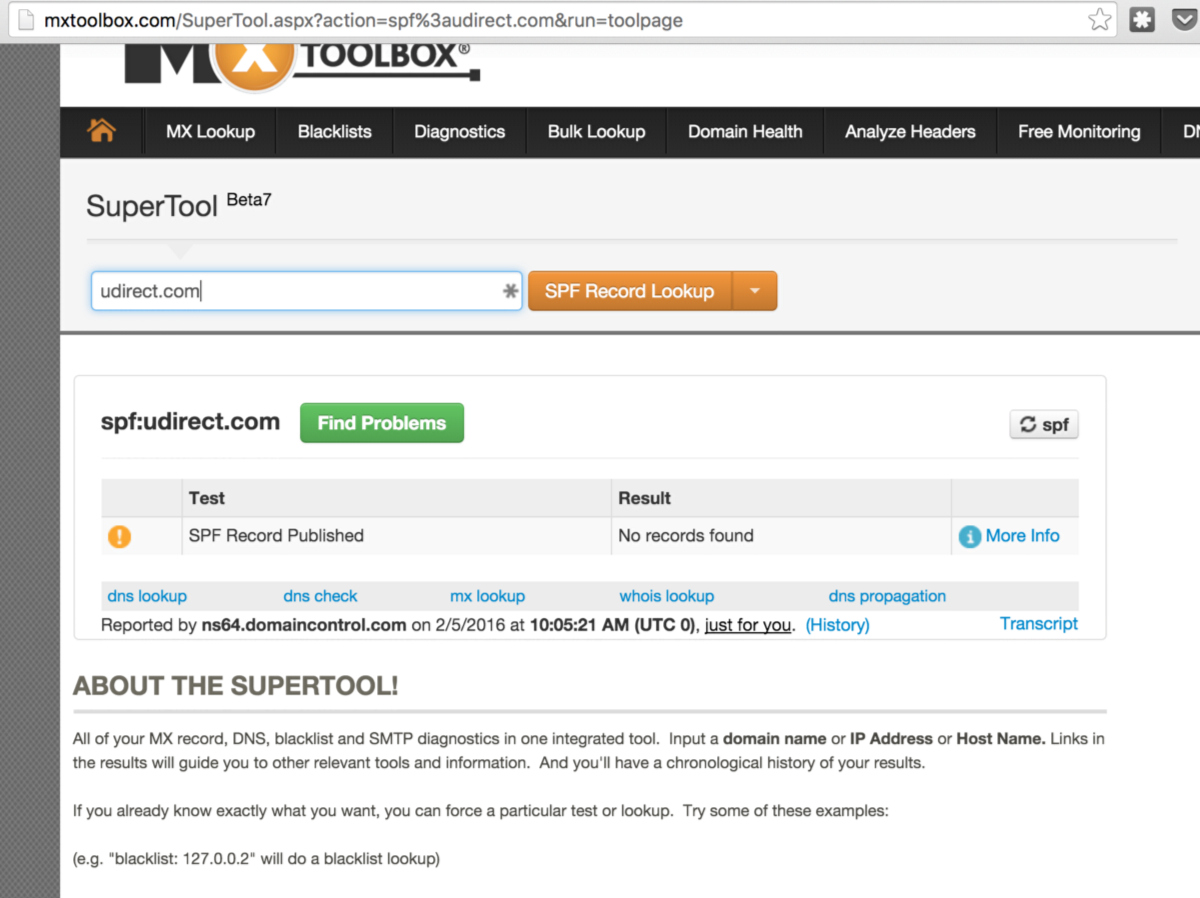
I was able to quickly report the fake ow.ly link to HootSuite and they have quickly taken down the suspicious link. Further digging up on the SPF records for udirect.com I was amazed that no single SPF record was in place. This means anyone can spoof the email address and send an email on behalf Udirect.com.
I was able to report the link and successfully shut down that particular campaign but there are hundreds of thousands of spam emails being sent every day and more people are falling into scams. There is little that individuals like me can do. I hope more organizations would really take information security very serious. I currently work as the Digital Security Lead at CcHub and working on an Osiwa project to help CSO's, Journalist, Active Citizens and bloggers protect themselves from Digital Security threats.
Article source : Medium
© 2011-2024 All rights reserved